Secure your Android Smartphone in 8 steps
About 97% of the french use a mobile phone, including:
- 55% use geolocation to their smartphone
- 67% connect everyday to a social network
- 46% store medical data
- 85% store of photos & videos
- 40% store very sensitive information (password, code credit card... etc)
In short, smartphones are filled with personal data or even very personal.
While in comparison to the sensitivity of the data, we learn that:
- 47% of smartphone users back up their data
- 71% download applications without reading the terms of use
- 9% have installed an antivirus
- 27% do not know to the neglect the locking of the smartphone
- 65% believe that their data are not well protected
Source: CNIL - study Smartphone survey.
65% of smartphone users think that their data are not well protectedCLICK TO TWEET
Smartphones are so full of very personal and very few protected.
Article today is thus intended to help you secure your smartphone Android.
Most of the applications presented here have been tested in order to ensure their quality.
Secure your Smartphone Android
Android represents about 70% of the market share of smartphone operating systems against 15 to 20% for iOS. It's a modern OS that allows not only send text messages but also to install all kinds of applications for us locate, process medical data and many others.
With the help of a tutorial, anyone can create an Android app. And then everyone can download it easily and for free. This ease of setting combined with a massive use by non sensitized individuals is an ideal entry point for hackers.
This is so the 8 steps to secure its mobile Android
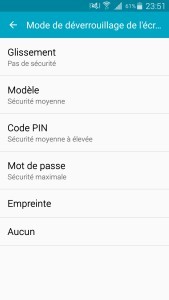
1. choose a complex locking
The lock is the first barrier of security against fraudulent use of our smartphone. It can be a lock code, of a model to draw, a reading of fingerprints or iris scanning. These methods have their advantages and disadvantages. Each option also has flaws, more or less patched. When there are no loopholes, it is a problem of complexity to unlock the phone for example by guessing the model or the password.
One of the typical problems of computer security arises: safety or ease of use?
These two criteria are often conflicting. Must he use long and complicated password that protects well against the smartphone party take 30 seconds to unlock the phone, or a model easy to draw but easy to guess?
The ideal is right amount. About the lock option to choose from, we usually recommend the password or fingerprint.
2. install antivirus
Install an antivirus for smartphone: for or against? This question is often at the center of the debate.
Some things are to know about antivirus for smartphones:
- Yes they stop any malicious applications, just as the computer with malware.
- Yes they require a bit more RAM/CPU consumption on your smartphone, like other applications.
An antivirus is still recommended and extra security.
This is among the best for Android antivirus. Note that it is unnecessary and counterproductive to to install several at once :
CM Security AppLock & Antivirus
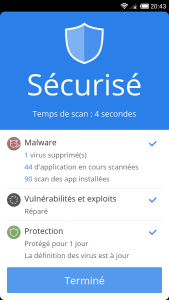
CM Security is one of the antivirus Android applications rated with more than 8 000 000 of positive opinions.
This application allows to:
- Lock sensitive applications by model or PIN code
- Scan files and applications mobile and SD card
- Clean unwanted files and browsing history
- Optimize the device
- Block calls
- etc...
Avast! Mobile Security & Antivirus
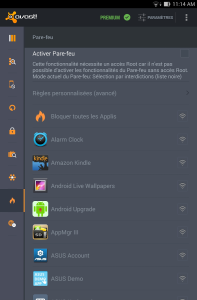
This is the Android version of the famous software antivirus Avast!
This application allows to:
- Scanning in real-time applications, files on SD card... etc
- Lock applications with model or code
- Save contacts, SMS... etc.
- Block applications through the firewall
- Find her phone in case of theft
- etc...
Lookout Antivirus & Security
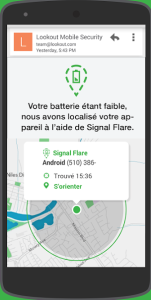
This application allows to:
- Scanner streaming applications against malware and other adware
- Find the device and an alarm in case of theft (with photo of the thief)
- Automatically save the position as soon as the battery is low
- Save and transfer contacts
- Protect the Internet navigation
- etc...
add applications (cleaning, optimization, security)
3. block the unsafe sources
The vector of infection number 1 in mobile devices is installing applications from unsafe sources.
Android applications typically end with the extension ".apk" and nothing prevents to share such an application via a web site outside the Play Store.
Blocking is usually implemented by default on most devices. You can still check on yours.
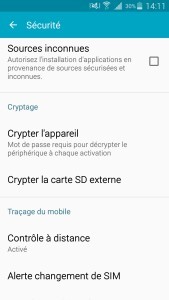
Your smartphone can also automatically connect to a wireless network not course, but also via Bluetooth or even NFC.
Keep these options enabled at all times is not recommended. So you can turn them on as needed via the parameters of the smartphone and not constantly.
4. encrypt its data
It also features more or less by default (see previous image), but if your phone does not have this option, you can use applications specially designed for this. Here are among the best rated:
SSE Universal Encryption App
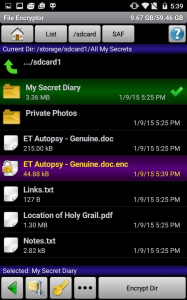
This application allows to:
- Store and manage passwords
- Encrypt messages as text
- Encrypt files or folders
- etc...
CyberSafe encryption
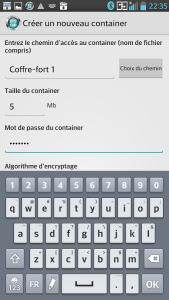
This application allows to:
- Create digital safes (records protected by passwords)
- Encrypt files over the network
- Allows to view/process files within the safe
- etc...
5. thinking about the loss or theft of the smartphone
Lose their smartphone happens often, sometimes even in our own room. But having stolen his phone a bigger problem and make a call will not necessarily find the thief. That is why there is the following application:
Where's My Droid
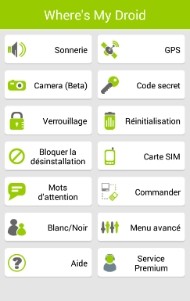
Where'is My Droid allows you to:
- Ring your phone remotely
- Receive the GPS coordinates of the phone remotely
- Lock the phone remotely
- Completely reset the phone (SD and SIM card) remotely
- Take photos remotely
All by sending SMS to the stolen phone. In addition to this, Where's My Droid also allows you to hide the application icon and prevent uninstalling.
6. ensure the use made of our data
During the installation of all applications Android (via Play Store), information is displayed about our data that the application will process.
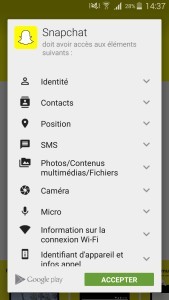
Some applications need some data for obvious reasons, while others ask the permission to use without really knowing why.
The ideal here is well aware that these data will be accessible to the application that can do what she wants.
It is for this that we recommend not to install applications without exact need.
7. save everything
A mobile phone stolen, data deleted by mistake or a fatal crash and your data is are sprayed for good.
Unless you did backups before. Some applications cited in this article allow you to make backups of your files, your mobile itself can offer this type of functionality by default.
But if you are interested in an application, this is one of the most popular:
Super SMS & Contacts Backup 
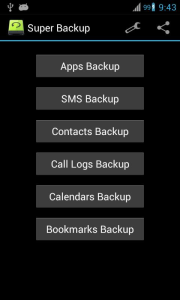
Backup is to do this not only through applications but also for yourself. For example the number IMEI and other codes should be kept in a safe place (and outside of the phone).
8. turn to day
It's one of the points most important. Update her phone and applications to address vulnerabilities. We too often imagine that update rhymes with 'new feature' while it also (and especially!) of patching the mobile or application against vulnerabilities.
The update also concerns us, keep informed (e) threats is a great way to not fall into a trap in the future. 90% of successful hacks actually exploit the weakness of human beings.
By the way, did you know that:
- Malware can spy on you even with your phone off
- Other malware can make calls from your phone without permissions
- Still others are extremely sophisticated (control distance, blocking of the uninstalls, ransomware... etc)
- Billion of Android devices meet regularly vulnerable to critical vulnerabilities (elevation of privileges, running code remotely... etc)









Post a Comment