Install a Vulnerable Lab for Kali Linux With a Router and VM
This small tutorial will allow you to install a vulnerable Lab to learn how to hack and make the pentest. In this tutorial I'll show you how I set up a network and a victim machine for my doing my tests of penetration.
To follow this tutorial need you a router and a wireless key. The router and the wireless key can optional era. If you have a router and Wi - Fi key you can move on to the second part of the tutorial but nevertheless will not network hacker but just a victim machine.
In the second part of the tutorial I'll show you how to install a virtual machine that you can learn to hack. Often I recommend VMware but to make a Lab but with VirtualBox Windows is easier and more complete.You will use VMware if you use a Linux lab with for example a website to hack. You can find victim Linux machines to download for free on the site in the relevant section.
Step 1: set up a network
I'll show you briefly how to install small network you can attack. If possible choose a model of router with broad and efficient administrations options (firewall integrate Wi - Fi draft N 3 antennas...).
Beware, there are more options, and more that will affect the price. A modem function is not necessary since it is your ADSL box that will provide the ADSL signal to the router.
Wherever your gateway to disconnect everything. For Linux type in a terminal:
Wherever your gateway to disconnect everything. For Linux type in a terminal:
root@kali:~# traceroute google.com
For Windows type in the command prompt:
C:\Windows\system32> tracert google.com
The IP address we're looking for and the first to be printed. In a small business network or home network IP address always begins with the two first series of turnip 192.168.X.X and finished by 1 or 254.
We must also find the address of sub network that starts always in compliance management with the first three digits 255.255.255.0. In Linux type in a terminal:
root@kali:~# ifconfig
For Windows type in the command prompt:
ipconfig /all
Do not close the command prompt or terminal because we will need from network information. Connect power to your router and connect the cable RJ45 from your PC to the router. Beware the RJ45 cable should not be connect to the WAN port but to the LAN. On many router the DHCP is enabled by default and assign an IP address.
To be about to have the defaults do a reset of your router by pressing the button in the hole with a toothpick or a pen. We should connect to the router via a browser interface. Type the IP address of your router in your browser's URL address bar. The IP address of my router is http://192.168.0.1 the vêtre may be different depending on your brand and model of router
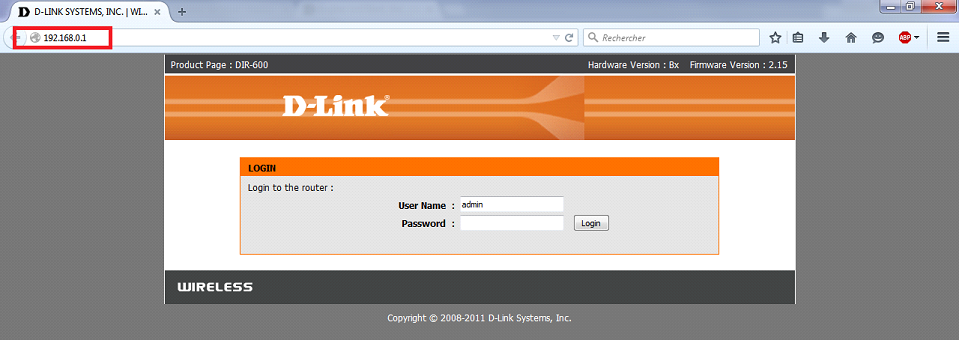

If you do not have this IP it is possible to find registered last router. You can also find from your manual. If you do not have the manual you can find it doing a search in google with the keyword "manual" and make more of your router model. Type the login and password you can find like your IP address, careful to get the login and password by default to work you must have done a reset your router. Little hacker trick, tried just in case the login admin with or without the password admin or administrator without password.
In the menu internet or Wan of your router configured the following options.
- IP address: address of the router on the network of your box, example 192.168.1.2
- SubnetMask: mask subnet found previously in your terminal or prompt order, example 255.255.255.0
- Rejuvenation: gateway found previously in your terminal or prompt order, example 192.168.1.1 or 192.168.0.254.
Attention to make your second network with your router work you must have a different network address in DHCP. For example, if the IP address of your BackupA is 192.168.1.x/255.255.255.0 then your router's network address will be 192.168.0.x/255.255.255.0.
In the end even if your IP addresses are different, you will have a network address range that looks like this:
Internet — [ip-wan/box ADSL/192.168.1.1] — [192.168.1.2/routeur/192.168.0.1/DHCP] — [192.168.0.x/PC]
When you're done you need to connect an Ethernet cable to the Wan port of your router to a port on your box. As it is highly unlikely that you have a second Ethernet port on your PC must configure a Wi - Fi network for the virtual machine. Before you start your virtual machine it will take from the host machine connect you to the router via Wi - Fi.
At the conclusion of part 1:
During your sessions of hacking your machine to attack will not be connected on the same network. For example your victim machine will connect to the router and your machine to attack on connect your Box. The goal is to successfully attack the victim on the other network machine as if you were trying to hack on the internet for example in thwarting the firewall of the router.
Step 2: Configure a PC to hack
You must first install VirtualBox or VMware.
Installation of a victim Windows machine
Installation of a victim Windows machine
Need you an ISO image of Windows and a license. dows.
Installing Windows in VirtualBox is very simple and in this tutorial the Windows installation procedure will not be detailed because this isn't the purpose and this tutorial. Just follow these steps key to make your victim of your pentest lab machine. Start VitualBox.
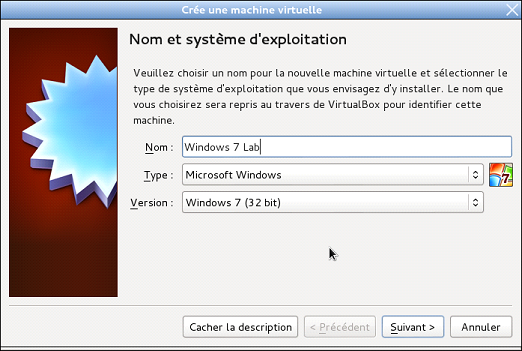
Name your Windows machine as in the example below, if possible set a minimum of 1024 MB memory live for not having too much latency when use you the virtual machine. Follow the procedure to create the virtual disk with set them by default so that you have a dynamically allocated disk.
Installing Windows in VirtualBox is very simple and in this tutorial the Windows installation procedure will not be detailed because this isn't the purpose and this tutorial. Just follow these steps key to make your victim of your pentest lab machine. Start VitualBox.

Name your Windows machine as in the example below, if possible set a minimum of 1024 MB memory live for not having too much latency when use you the virtual machine. Follow the procedure to create the virtual disk with set them by default so that you have a dynamically allocated disk.

Once finished you revoil before the main VirtualBox window. Before to start installing Windows follow this important step.
In the main VirtualBox window, click Configuration. Head in the network menu. Enable the network card with the access network by bridge (bridge) mode.
If you have installed a router as explained in step 1 then use Wi - Fi by sectioning the Wlan0 (Wi - Fi) network card. Attention before starting your virtual machine must connect to the internet from the host to have Wi - Fi network.
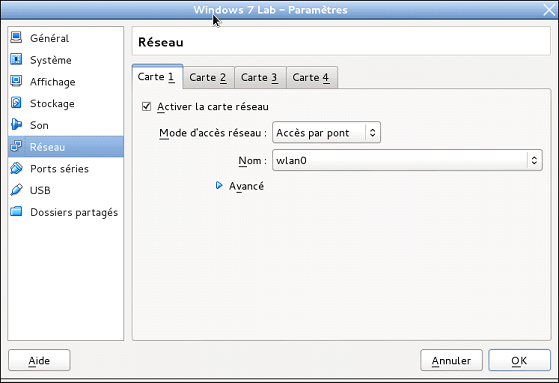

Subsequently made other configurations necessary for the installation of Windows and start the installation.
Install Windows as usual but beware we do a vulnerable machine and not secure then install any update. You can ride the difficulty of the challenges by installing a service pack of Windows. Then choose configuration of the network share, domestic being easy to attack and public level more secure, you choose.
When the Windows installation is complete you need to install a user environment. Indeed your Windows machine is blank what is going to be a problem as to attack a machine on a network it takes what's services or at least software that open ports or modifies the system.
To install quickly a user environment log onto this website-online https://ninite.com

When the Windows installation is complete you need to install a user environment. Indeed your Windows machine is blank what is going to be a problem as to attack a machine on a network it takes what's services or at least software that open ports or modifies the system.
To install quickly a user environment log onto this website-online https://ninite.com
What should I install? Actually all, installing more than one-half to recreate a real user environment, careful not to overload the useless machine with too much ligiiel. The Security category is to customize according to your tastes and your challenges, but if you are new then install no security system.
You can see the ports opened by programs with the command prompt by typing:
You can see the ports opened by programs with the command prompt by typing:
C:\Windows\system32> netstat -nb
Caution you must open the command prompt in administrator mode. Why are there not more open port? This is probably that not a lot of open software. Open a software to see if the ports open.
Protect your machine from crashes
Finally, I recommend you to install these applications on your virtual machine.
ToolWiz Time Freeze
ToolWiz Time Freeze
Toolwiz Freeze Time to not make unwanted changes on the system. Whatever changes you make, no matter what happens, a simple reboot put things as she was. When Toolwiz Freeze Time is up and running changes to the system will be cancelled, download files will be deleted, and other undesirable changes will be cancelled when you restart your PC hacker. Can you freezer your machine with a simple click and leave the freeze mode with a simple reboot or shutdown of the PC hacker.
Sandboxie
Sandboxie puts at your disposal a virtual space (the Sandbox) to test applications, browse the Internet and manipulate files safely. Indeed, the items handled in this safe space cannot reach the hard drive. This Sandbox can be a tool of anonymity and protection against attacks and intrusions. A Manager allows to list active processes, administer the content of the Sandbox and create other secure areas. Sandboxie is a paid software limited to 30 days. The trick to use it to le delas 30 days is to download the software and save it. After your machine with Toolwiz Time Freeze freezer simply install it to use it to the infinite.







![[Darknet] How I Discovered It, and How to Access](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEigkvDILsG9sBTqEktFANKPS5HYpz1I4Cn00RhSPezewjQjxnKrznkJmBvWUnLHTrH_5_OibNQhzXA1HoPOKuhMOWkc5kaeA4QKpx5t24CS8rdr8YPqUGT4t8HogBdnS7Txj8p9AQZU7I0/s72-c/%255BDarknet%255D-How-I-Discovered-It%252C-and-How-to-Access.png)

Post a Comment